Thursday, December 12th – 6:12pm @ Discord
Hello Hackers!
This last month of 2024 we are joined by @Bajiri who will be presenting their talk “Bypassing EDR Constraints via WSL 2”:
Windows Subsystem for Linux version 2 can be utilized to bypass logging and detection, as well as network containment functions, of a major EDR vendor. This bypass is incredibly simple to execute, and several rounds of escalating tests show that this flaw in monitoring is easily exploited to execute malware on the host device undetected. When contacted about this issue, the vendor said they don’t support WSL2 or have any plans to fix their broken network containment /shrug
I am a SOC analyst, but I spend most of my time brain rotting in front of a computer and getting paid for it. I really like writing and researching malware too! Any time I am not doing cyber things, I’m usually playing FFXIV or other MMOs.
Meeting will be on Discord. If you need an invite, look no further.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
Thursday, November 14th – 6:12pm @ Discord
Hello Hackers!
This month we are joined again by repeat speaker and general tinkerer @r1otctrl who will be presenting their talk “Laser Rat Labs” which consists of, quite simply:
Lasers, ducks, rapid prototyping, and more lasers
Meeting will be on Discord. If you need an invite, look no further.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
Thursday, October 10th – 6:12pm @ Discord
Hello Hackers!
This month we are joined by first-time speaker and new DC612 member Macros who will be presenting their talk “Automated Malware Analysis”:
Overview of CapeV2 and Automated Malware Analysis. A bit of history of Cuckoo and its evolution into Cape. Basic Usage and features. Demoing various malware samples on a Windows 10 box. Overview of analysis of the samples.
Meeting will be on Discord. If you need an invite, look no further.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
Thursday, September 12th – 6:12pm @ Discord
Hello Hackers!
This month we are joined again by @MiloSilo_Hacks who will be presenting his talk “Gpt4all is neat for AI. Try it”:
Learn how to install gpt4all and dive into RAG (Retrieval-Augmented Generation) AI. Usage best practices will be included!
Meeting will be on Discord. If you need an invite, look no further.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
2024 Toxic BBQ September 21st!
Hello hackers!
We have exciting news: The 2024 DC612 Toxic BBQ is on!
Big thank-you to Marie for purchasing the permit this year!
- When: Saturday, September 21st from 4PM to 10PM Central
- Where: Minnehaha Falls Regional Park, Wabun Picnic Shelter F (map here)
- 4655 46th Ave South, Minneapolis MN 55406
- NOTE: This is a different site from the last two years, but it’s right next to it. About 100 feet North, give or take*.
- What:
- Food! Bring food and we will grill it, or just show up and eat.
- Hackers! We have been told there may be hackers in attendance.
- Music? Games? Prizes? Stickers? Whatever you bring!
Beeeeeees!Due to budget cuts, we will not be providing bees this year.
- Cost: Zero dollars!
This is a group-led event, so it is only as good as we make it. We have a sign-up sheet here to track what everyone is bringing, please fill it out if you plan on bringing stuff. Please note that canned beer is allowed, but no other alcohol per permit rules We are waiting to hear back on the alcohol front. We always need food, but paper plates, plastic utensils, and napkins never go out of style. If someone wants to bring musical entertainment, or games, or a vulnerable WiFi spot, all the better!
Nobody is required to bring anything or pay anything to attend and eat, but keep in mind that our official budget is also zero dollars, so we will only have what we all contribute.
This will be our fourth year running:
and we’re hopeful to keep this tradition going for even longer.
See you all there!
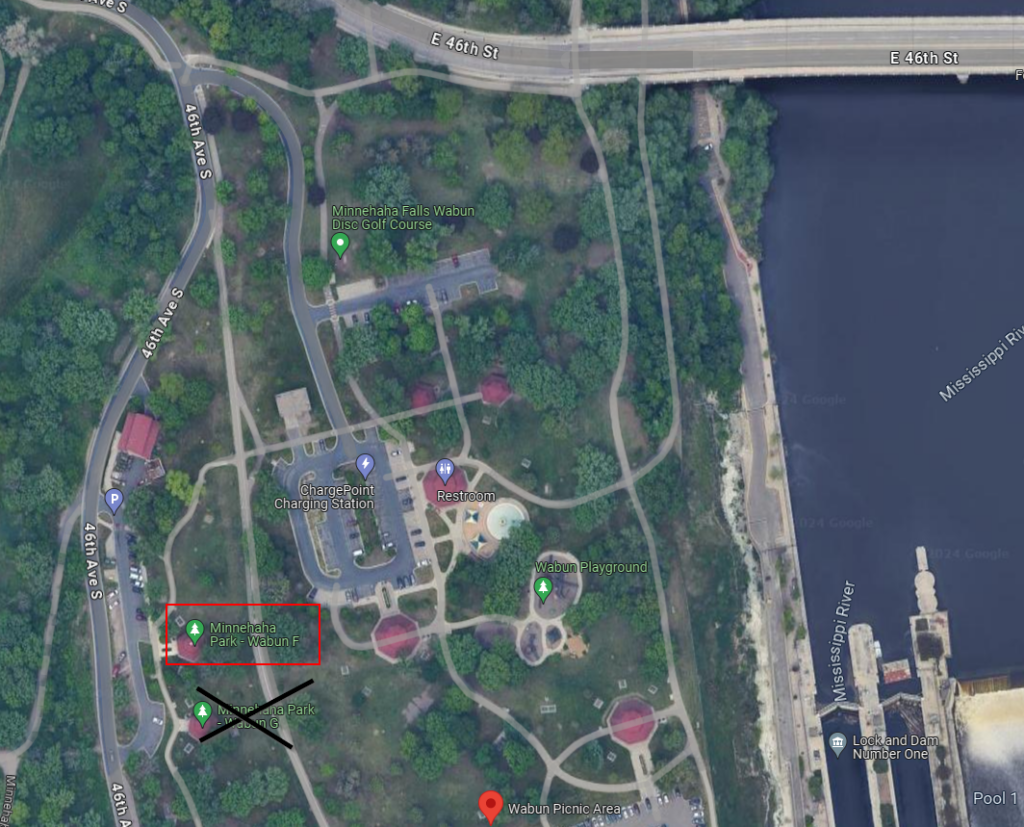
* My calculations for the distance are as follows:
On Google Maps, I zoomed in as close as I could to get the best picture of the two sites. The scale on the bottom right shows that 20 feet are represented by 117 (113 + 2 on each side) pixels:
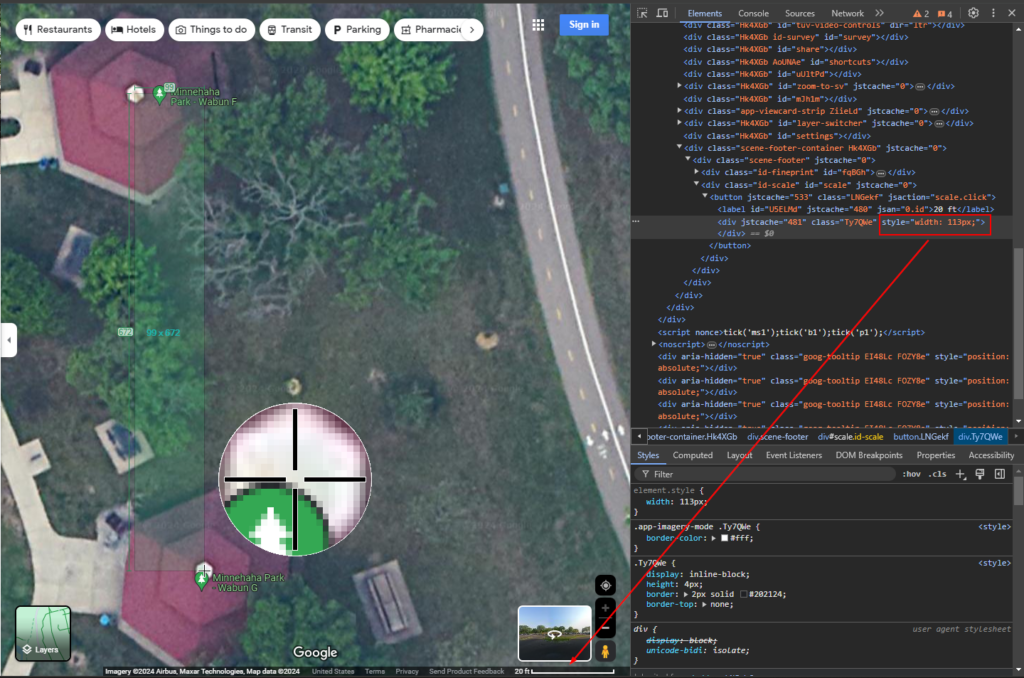
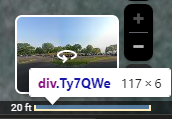
I used Greenshot to measure the distance between the two sites and found that they were 99x by 672y pixels apart. Some quick math:
99 / 117 = .846 * 20ft = 16.9 ft West
672 / 117 = 5.744 * 20ft = 114.9 ft North
The straight-line distance can be solved thanks to our friend Pythagoras and ChatGPT:
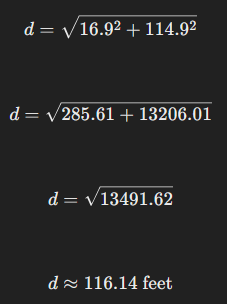
So they are 116.14 feet apart.
As to the compass direction, a 32-point compass will define 7 points between North and West:
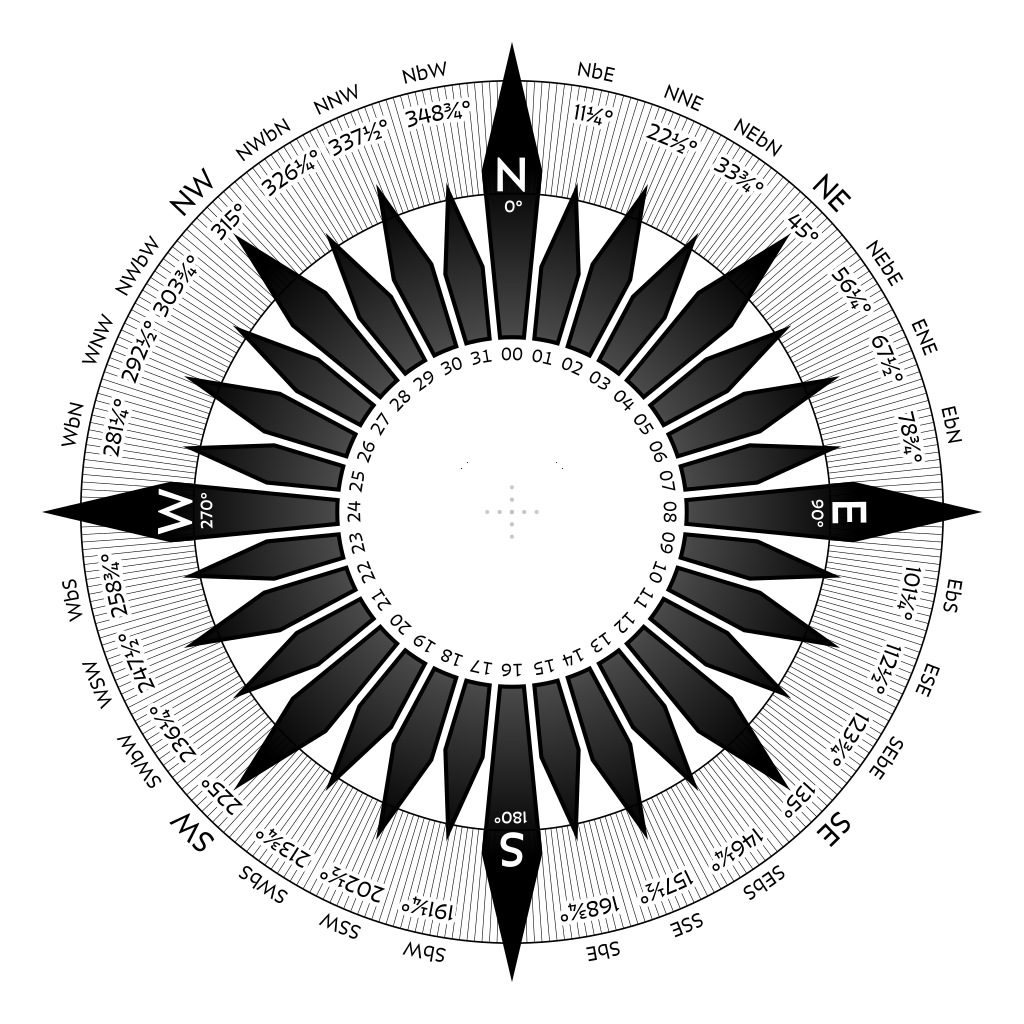
According again to ChatGPT (I am not awake enough to math this myself) you can use the following calculations to get the angle from North:

Since each point in a 32-point compass represents 11.25 degrees, that would put us at NbW, or “North-by-West”, since 8.39 is less than 11.25 but greater than the halfway point between North and NbW (11.25 / 2 = 5.625).
So when I said “100 feet North” earlier, I apologize if I offended any sailors or land surveyors who may have expected a little more precision.
QED
