Uncategorized
Thursday, September 8th – 6:12pm @ Virtual
Hello hackers!
This month’s meeting is mostly going to be a panel-style DefCon recap from those who attended either virtually or in-person. Badge talk, contest talk, village talk, talk talk.
After that there will be some planning for the upcoming DC612 Toxic BBQ.
Real chill this month.
As usual these days of Covid, we will be meeting online at https://cafe.cyberia.club/dc612.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
2022 Toxic BBQ September 17th!
Hello hackers!
In addition to having our September speaker lined up (details in a future post) we have exciting news:
The 2022 DC612 Toxic BBQ is on!
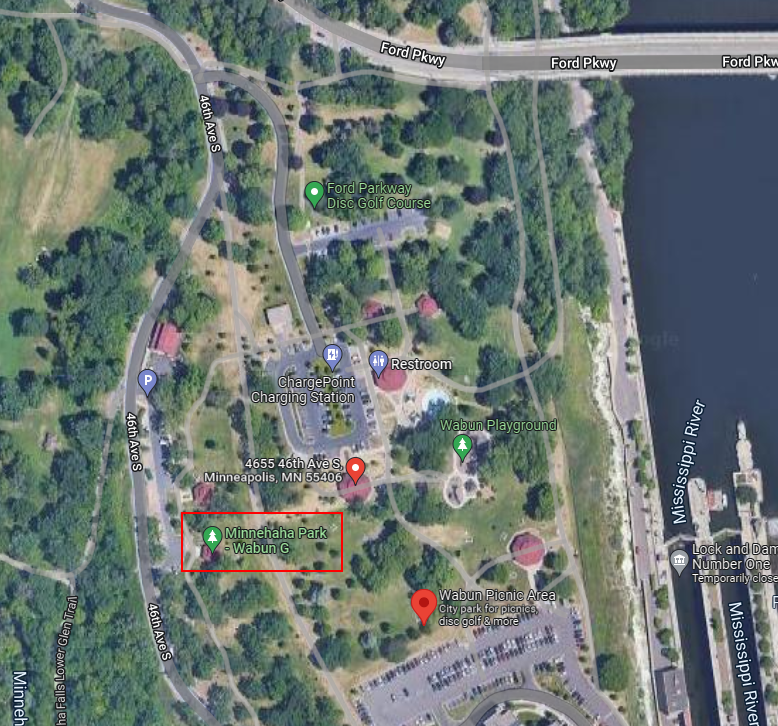
- When: Saturday, September 17th from 4PM to 9PM Central
- Where: Minnehaha Falls Regional Park, Wabun Picnic Shelter G (map here)
- What:
- Food! Bring food and we will grill it, or just show up and eat
- Hackers! We have been told there may be hackers in attendance
- Music? Games? Prizes? Maybe!
- Cost: Zero dollars!
This is a group-led event, so it is only as good as we make it. We have a sign-up sheet here to track what everyone is bringing, please fill it out if you plan on bringing stuff. We always need food, but paper plates, plastic utensils, and napkins never go out of style. If someone wants to bring musical entertainment, or games, or a vulnerable WiFi spot, all the better!
Nobody is required to bring anything or pay anything to attend and eat, but keep in mind that our official budget is also zero dollars, so we will only have what we all bring.
See you all there!
Thursday, July 14th – 6:12pm @ Virtual
Lets gather this month to celebate Fête nationale française! otherwise known as Bastille Day. What does Bastille Day have in common with our speaker this month you ask? Well, nothing but I’m sure we can come up with some correlation between Kratom and the storming of the Bastille.
This month we are joined by local scientist and opioid researcher, Pthamm. They will bring us all up to date with the latest research on Kratom – what we know from the peer-reviewed published studies and what we don’t.
Pthamm will answer questions like “What are the claims people are making about Kratom and what can the science say about those claims”. Pthamm read the peer reviewed scientific studies so you don’t have to!
As usual these days of Covid, we will be meeting online at https://cafe.cyberia.club/dc612.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
Hope to see you there in your Blue, White and Red!
-Kat
Thursday, June 9th – 6:12pm @ Virtual
Hello Hackers!
This month we are joined by @NightmareJS who will be presenting “How Ransomware Can Follow You to the Cloud”:
Ransomware is a financially motivated crime. The goal is to inhibit business system in order to extract a payment. Historically, there’s been plenty of financial gain from ransoming data as it resides in traditional onPrem systems. So the question is, will there be evolutionary pressure on attackers – forcing them to evolve tactics?
In this talk I will be demo-ing strategies threat actors might employ to affect availability of business data in the cloud.
As usual these days of Covid, we will be meeting online at https://cafe.cyberia.club/dc612.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
Thursday, May 12th – 6:12pm @ Virtual
Hello Hackers!
This month we are joined by David Tippett who will be sharing a hardware project, with a presentation titled “Solving Trivial Problems with Facial Recognition”:
Remembering people’s names is a basic life skill. A life skill I really suck at. I will remember someone’s face forever but after a few days of not seeing someone their name starts to fade from my mind. Even if I’ve known them for years it just vanishes into thin air.
Naturally, the only way to solve this problem is writing a data pipeline and hacking together a complicated wearable with a heads up display to tell me the name of who I am conversing with. While this may seem ridiculous (which it is) there are so many ways that we can begin to use technology to enhance our lives that haven’t been discovered because people are too comfortable with the way things are.
As usual these days of Covid, we will be meeting online at https://cafe.cyberia.club/dc612.
Talk starts at 6:12 PM U.S. Central, but feel free to hop in early and chat.
— TactiFail
